[#62] Your apps are spying on you and privacy laws don't seem to care enough to enforce or regulate it
DPDP & GDPR protect obvious data like phone numbers and bank information, but don’t stop or regulate apps from profiling users by silently querying installed apps in the background
With the Digital Personal Data Protection (DPDP) Act being passed in 2023, India finally has the foundations of a formal privacy framework. Yes, the rules and procedures are still being drafted, the Data Protection Board isn’t fully functional yet, and enforcement remains a work in progress, but it’s a start. A positive one. And hopefully, even though the law doesn’t address anything of this sort, it’s a step toward ending the relentless spam calls and messages trying to sell you personal loans, apartments, insurance policies, and god knows what else.
The Act covers the right themes: user consent, data usage, transparency, management, and penalties. But here’s the problem, it still feels directional. The fact that this was drafted and released in 2023, and we still seem to be a ways away from actual implementation & enforcement of the same is worrying. It outlines principles, not specifics. And some of the gaps in it: things that are not explicitly stated but instead indirectly covered such as AI profiling, data portability and backend app querying leave a lot of “grey area” for organizations to operate in, something that they excel in.
And that’s exactly what the DPDP Act needs to protect consumers from.
The obvious stuff is well understood: Don’t share financial or health data without consent. Store it securely. Encrypt it. That part makes sense. But here’s the catch — nearly every major app today is turning into a fintech or a payments product, even if that’s not what they were originally built for. And once they integrate UPI, they suddenly have access to a large chunk of your financial activity — enough to infer your income, spending behavior, and creditworthiness.
What’s going to separate these players now is alternate data. And the ways some of them are collecting it? That’s where things get worrying.
But more on that in a bit. Before that, let’s try to understand what exactly the DPDP Act does protect, and what are some things that are not mentioned (especially in comparison to the EU GDPR Act)
A quick summary of the protections of DPDP Act (full doc can be accessed here)
User consent for data processing: Explicitly called out, and being able to withdraw consent should be as easy as giving consent. What people call “the right to forget.”
Notice to users about how the data will be used: Explicitly called out. Must precede data collection and detail the data, purpose, rights, grievance mechanism BEFORE the data is collected, and can’t be buried in some jargon (terms & conditions docs of amazon, meta, and apple come to mind). It has to be in plain language.
Data rights of the user: At any point the user whose data is stored can be accessed, corrected or erased by the user and there is proper grievance redressal
Monetary penalties of upto INR 250 Cr for a single breach under the act
Children data rights: no ads, and requires parental consent
Things such as App Querying, SDK & Embedded Tools & AI profiling are not explicitly called out, or are absent from the draft
App Querying: It’s indirectly covered I suppose under user consent & personal data misuse, but it’s not explicitly called out. I’ll get to why this is a MASSIVE issue in a bit. What is App Querying? It’s the ability of an app, let’s say Swiggy to be able to check what other apps are installed on your phone
SDK & Embedded Tools: There are embedded tools (if you download specific App APKs you’ll see SDKs embedded: clevertap for example is for marketing, Juspay for payments. These tools do collect a lot of personal data. Who does the liability lie on here?
AI profiling and automated decision making: While profiling of children is explicitly forbidden, the profiling of adults is not. So I may be able to infer things from location, or behaviour are covered. Compared to the EU GDPR this is a pretty big miss. Why is this important? It’s because based on some structure / program that a company puts together, consumers can be subject to unfair biases, and lack of transparency (ex: Why didn’t I get that job, or why was I denied a loan?). Under GDPR the consumer has the right to object to profiling, to human intervention, to being informed, and the right to NOT be subject to AI profiling. But not under the DPDP.
Data portability: under the GDPR if I want to switch providers, let’s say I want to switch banking providers, or even things such as my music app, I can download it from one app and upload to another. This is not something that is allowed under the DPDP Act, so it reduces the consumer's freedom to switch. From the merchant perspective it’s great though: high switching costs = tougher for the customer to move to competitors
Internal Company Access to Data: This is implied, not mandatory. What does this mean? I’ve worked in start-ups. While some may not have the best of consumer intentions at heart, most do. But the start-up ecosystem in India has matured now. We’ve already seen the first wave of start-up IPOs, with Paytm, Zomato, Mobikwik, Nykaa, Swiggy and so on, and the next wave of start-ups: Pine Labs, Groww, Razorpay, Zepto to name a few are preparing for the same. Most have been operating for 8+ years now. And a lot of these are B2C & B2B2C offerings, which take in , and have access to a large amount of consumer data. Even within the company, who is accessing this data? What checks and balances are put into place? Is the data encrypted and stored in the database? In a lot of places, it’s not. If you have access to the database, then you have access to non anonymized customer data, which is a massive red flag!
This whole issue with App Querying has been covered in Pea Bee’s substack → and its clear that for a lot of apps, knowing which other apps are installed in your phone, and using that to create a user profile for cross sell products, or even sell this to 3rd party applications is the new data play
I recently read an interesting article by Pea Bee (substack here), specifically the piece about how everyone knows the apps on your phone. Here’s the link below. It’s eye opening, and I personally was shocked (although from what I understand, this is somewhat of an open secret). I highly recommend everyone read it.
TLDR, the author of the above substack has done a deep dive into the Android App Ecosystem: specifically the information that apps are collecting on the user.
Until a few years ago any app installed on Android could see all the apps installed on your phone. But ever since 2022, with tightening security protocols, apps can query those apps which are essential to core functionality. Developers must also explicitly declare these apps in the AndroidManifest.xml file - a required configuration file for all Android apps.
Now it’s worth noting that for some apps, to provide a better experience, they should know the apps installed. A key sector here is payments (and one that is close to my heart). To provide an optimal payment experience, if I’m buying something on let’s say Blinkit, if the app can check which UPI apps are installed, and show those as preferred payment options at checkout, then that 1) helps the merchant to convert the customer and reduces drop offs and 2) optimizes the experience for the customer. According to the substack, some apps: Swiggy, Zepto, KreditBee check for the presence of over 100 apps on your phone. KreditBee checks for 860 Apps! And while these include apps such as Paytm, GooglePay etc, this also includes apps such as Spotify, Starbucks, and things such as Ludo, Carrom, and Dream11. What use does a lending app, and grocery delivery apps need for all this information? It’s obvious: by querying these apps, you can create a profile of the customer, and change prices, recommend different stuff, and essentially ‘spy on the customer.”
Chinmay & I couldn’t believe it: that apps have access to all this data. We tested it out for ourselves on both iOS (IPA) and Android (APK) apps
Note: The section below is if you want to extract / download the IPA / APK file & examine it yourself. To check it out for yourselves, you can access the website Chinmay built for this. To see what permissions and different apps, one specific app is querying and asking for, extract the APK or IPA file of any app, let’s say Swiggy from your Android, or your iPhone, upload it into the website. You can also just get app IPA from here, and APKs from APKMirror. If you already are familiar, then you can skip to the next section where I’ve pulled the data on which apps are querying for what.
Get APK / IPA and upload into the tool that we built
Mobile App Analysis tool: here
Steps:
Download your APK / IPA from APKMirror or Decrypt.day OR
Extract the app APK / IPA from your phone
Select if its APK (Android) or IPA (iOS) and upload it into the website
See list of permissions & apps the uploaded app can silently query
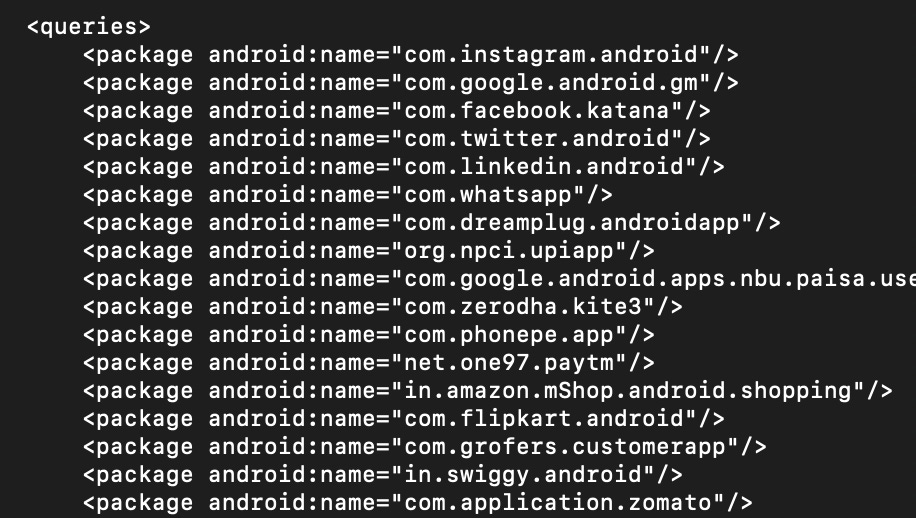
Screenshots attached of Zomato IPA file downloaded from Decrypt.day
After uploading the Zomato IPA you can see the list of permissions it asks for in the permissions section, and a list of apps it can silently query in the “Query Packages” section. This includes competitors like Swiggy, payment apps such as Gpay, Paytm, but also apps such as Gmail, Cleartrip, and Oyorooms. And the list is bigger (details in below section), this is just a snapshot
For those of you who want to check it out by extracting apps from your phone and querying it yourself:
If you do want to extract it specifically from your phone, which can be better if you want to decompile and examine the latest version, and see what it is specifically doing on your phone then you can do it for both Android & iOS in the following way.
I’d recommend that if you’re deep diving and actually want to know, it's better if you extract it from your phone since it’s possible that some of the APKs available for public consumption may not really tell the whole story have not done the requisite declarations of what apps they are querying in the public APKs.
Example: As per Pea Bee’s analysis (which is super detailed), they have also published the Android xml files of multiple Indian Apps on github (you can check it out here).
And they did this after installing the Android app from the app store instead of downloading from public sources: Zepto queries more than 100 apps. As per the public APK downloaded from APKMirror (which btw was uploaded by KiranaKart technologies which is Zepto’s registered name) the list of apps queried are ~20. The screenshot below is from the public APK downloaded. Not shown in the list are also Truecaller and Tata Neu:
Note: There are probably better ways to do this so for the experts out there, you probably know more efficient ways to do this. I’ve done this using chatGPT, macOS Terminal and “vibe coding.” I’d recommend that after you extract the file, using the tool Chinmay has built since it’s way easier.
1) Android App Extraction and checking the Android Manifest File
For Android APKs, you can use Android Studio to extract the APK and get manifest.
But there’s another simpler way. You can either download a sample APK from Apkmirror or download an APK real time from your Android phone (chatGPT all the way), and query it. The file in an APK that contains a list of all the apps that are installed is called the Android Manifest file. To see this list, you can use Terminal on your Mac, navigate to where the file is on your device, unzip it, and then look for the android manifest file. Note: you’ll need to download apktool for this (which you can do through the Terminal in macOS) since that helps to decompile APKs into human readable resources.
For MacOs to install apktool on your laptop you can use the below command in Terminal:
brew install apktoolThen after that, follow the steps below (here the file is saved as Zepto.apk, and I’m saving the unzipped file as “zepto_decoded”:
Decode APK: This will create a folder called zepto_decoded with all the extracted content, including the manifest.
apktool d "Zepto.apk" -o "zepto_decoded"This will navigate to the unzipped file, which as per the previous function we’ve named “Zepto_decoded”
cd "zepto_decoded"Open the list of apps that can be queried in the Android Manifest file of the APK:
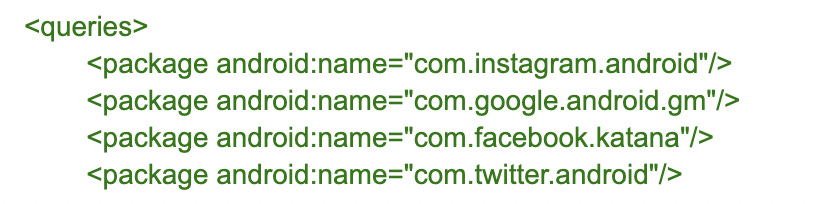
grep -A 50 "<queries>" AndroidManifest.xmlAfter searching for “queries” this command tells me to capture the next 50 lines of code, which is the list of app queries. Example, if I had used grep 10, it would have captured “queries” and captured the next 10 lines, which shows the 10 apps that are queried. Usually good to keep this number as 50 or 100 to make sure we’re not missing on anything. Example output is below:
2) iPhone: Extracting the app IPA from your Iphone and vibe coding the extraction:
I have an Iphone, so I was keen to see what personal data the apps I’ve installed are collecting on me. I downloaded a tool called iMazing that allows you to store backups of your Iphone Apps. Once you create a backup - depending on the amount of files, this can take 1-2 hours. After you create the back-up you can navigate to the app section of iMazing, download the app, and then export it as an IPA file onto your desktop.
After this, I ‘vibe coded’ to see if I could extract the info-plist file and see which apps are being queried in the back-end. Take the example of Atlys, which was one of the apps downloaded on my phone. I exported the IPA file from the back-up on iMazing on my desktop, and then used Mac Terminal to see the app queries under LSApplicationQueriesSchemes (this is the iOS version of queries in the Android Manifest File). This is how I did it, and for those of you who are interested, after extracting the IPA you can follow along below or vibe code using ChatGPT.
Navigate to the IPA file. (in this case it’s saved on my desktop)
cd ~/DesktopAll IPA / APK files are zipped, so you can unzip it:
unzip “Atlys.IPA” -d “Atlys_extract”Once you unzip it, you can navigate to the Payload file within the app
cd “Atlys_extract” / PayloadWithin the Payload file, you navigate to the .app Folder
cd Atlys.appNow within this folder you navigate to the LSApplicationQueriesSchemes segment to see what apps it can query in the backend. The LSApplicationQueriesSchemes is the like <queries> section of the AndroidManifest file
grep -A 20 “LSApplicationQueriesSchemes” Info.plistYou’ll get an output that will look like the below:
Under the <array> element, each line is an app that is being queried. For Atlys, these are the apps it is querying the backend. Most of them are payment apps: Phonepe, Googlepay (Tez), Slice UPI, BHIM and so on. Some I would question a bit, such as Instagram & Whatsapp, but nothing too shocking. My bigger concern is that at no point when I downloaded Atlys, or any app for that matter, did I know, or was I asked for permission that Atlys (or others) were checking for the presence of the above installed apps on my phone.
The goal? Profiling. Targeting. Ad tech. Behavioral analytics.
And by the way, the above ways that Android has adopted of getting apps to declare which apps they are silently querying is still better. Earlier Android had no restrictions, any app could silently scan your list of apps.
Apps would use the below, and scan all your installed apps silently.
PackageManager.getInstalledApplications()Now atleast there is a requirement to declare it in the AndroidManifest file under the <queries> block. But this is within the app file. You have to dig to find this. It’s not “common knowledge.” It’s not surfaced to the customer. Even though Android added restrictions, many apps over-declare in <queries> to get around them, and Google rarely enforces this strictly, especially on big apps like Zomato, Paytm, etc.
There’s another loophole in Android’s policy: “Querying by intent” where you can check to see what apps can open a certain type of link, without having to actually declare them in the Android Manifest file.
One way to silently scan for apps on your phone is to declare it in the AndroidManifest file. Another way to do this is “querying by intent.” What does this mean? Well, apps on Android don’t just launch other apps randomly. Think of when you’re making a UPI payment on lets say Zomato. It doesn’t just launch Phonepe. It first queries by intent for payment apps, which means it sends a request to Android’s operating system to check what others can handle the payment request. The OS checks, and then sends the response back to the querying app. It’s like asking: Hey, who on this phone is capable of handling a upi://pay link? Other examples are:
“Who can open http://maps.google.com?” → gets Maps-type apps
“Who can open mailto: links?” → gets email apps
And you never see a permission screen for this EVER!
This is very invasive: and also answers the question of differential pricing based on the type of phone and even situations. It’s essentially customer profiling without the customer consent
There have been multiple public conversations on how Ola & Uber can manipulate prices if you’re using both apps together, or Zepto gives differential pricing if you are on an Android or iOS. They’re able to also do this because of the visibility they have. And they’re building their customer persona based on this. While Atlys - the example I used above doesn’t have anything too crazy, Zomato has some questionable apps it’s querying. For Zomato I wasn’t able to export the backup IPA file, so I downloaded the Zomato & Swiggy IPA’s from Decrypt.day and then examined it further.
Why do Zomato / Swiggy need to know if I have Fantasy Gaming, FirstCry, or Unacademy installed on my phone?
As I said, wanting to know the existence of specific Payments App, is a logic I understand. But why does Zomato need to know if Oyorooms, unacademy or Ballebaazi, a fantasy gaming app, is installed on your phone? Seems ludicrous! Swiggy queries for FirstCry, which is a platform to buy baby products. Probably so they can give relevant suggestions for parents with infants. But this can also be dangerous, and lead to bias based on gender, pregnancy, and other things. What if a loan app decides to increase a woman’s interest rate because she has a kid? Or an insurance app gives me a higher premium?
Discrimination can even happen based on race / your hometown and so on. For example, if I hail from a specific part of India. I may have downloaded some app that can allow applications to infer this. Example -> there is an app called Baduli Music on the ioS app store for music from Himanchal Pradesh and Uttarakhand. This could provide a pretty accurate indication of where someone is from, and could give rise to discriminatory tactics. I’m not even going to get into fintech apps: I expect some lending apps to be even worse.
Reportedly iOS has more security as compared to Android. And if I compare APK & IPA files of the same app (downloaded from my phone not a public source) it looks like more apps are being queried on Android vs iOS
As per the documentation on developer.apple (link here), “Apps linked on or after iOS 15 are limited to a maximum of 50 entries in the LSApplicationQueriesSchemes key. Which functionally means that they can silently query for upto 50 apps.
Example below checks for 3 apps -> Whatsapp, Paytm, and Gpay. (3 entries in the SApplicationQueriesSchemes Key). If there are more than 50 entries, then apple will reject the build (note: this is for apps linked to iOS 15 or later):
iOS Example below: Limits silent querying to upto 50 apps
Android Example below: Can silently query upto 1000 apps
Compare that to Android documentation for Android Manifest. The limit is not explicitly stated (atleast, I couldn’t find it), but from what I understand, the limit of child elements under the <queries> element is 1000. So theoretically, you can query a little less than 1000 apps: Example, below are 4 child elements under <queries>
So clearly, iOS limits this to a greater extent than Android.
iOS is considered to be a premium product: Seems to imply that data security is a premium feature and not a basic right
There are 2 questions that then arise.
The bar is in hell. Apart from “experience based stuff” like payment apps, why should an app know anything about the other apps I’ve installed on my phone? And why am I not explicitly being asked about it, be it Android or ioS? Why do I have to go through all this -> downloading the IPA, decompiling it and then checking the files to see what data is being exposed?
iOS is considered to be a premium phone. Not to say there aren’t premium versions of Android. There are. But overall, from a mass-y perspective, there are way more affordable android smartphones vs iPhone. Do we mean to say then, that data security is a “premium” feature, and not a basic right? Seems classist.
At this point, I don’t care about who has my mobile number and email. But this sort of access, user profiling and then automated decision making (and probably even user profiling selling) scares me.
At this point, I honestly don’t care who has my phone number or email anymore. I've signed up for too many apps, especially in payments and finance, and many of them are far from what you'd call "consumer-first" apps like Ola, Zepto, and others have likely already sold or shared my data. I never asked Bajaj Finserv for a loan, yet I get regular spam calls from them — and from half a dozen others trying to sell me something. This is what I consider first-level data: contact info, basic identifiers, the stuff that’s already out there.
What I expect, or at least hope for from the DPDP Act is a way to retroactively put some guardrails in place. A mechanism to report misuse of my phone or email, and for meaningful action to follow. Because the truth is: even if I don’t give you my contact info directly, you’ll probably buy it from someone I’ve already trusted knowingly or unknowingly.
But what worries me more is the second-level data, which is my behavior. My location history, where I eat, what I browse, how I shop. That’s the layer I absolutely do not want shared or traded. My financial statements, my health data - those are obvious, and in theory, already protected. Between UPI, the Account Aggregator framework, and explicit digital consent flows, that ecosystem at least feels like it has some structure. To check out my piece on India’s Account Aggregator Network, see the link below:
The problem is everything that happens in the background. The inferred data, the silent profiling, the algorithms making decisions about me without my knowledge. Apps querying what other apps I have installed, piecing together a behavioral footprint, and then automating decisions like whether I get a loan, at what rate, or whether I see a certain price.
Take KreditBee. Their APK reportedly can silently query over 860 apps. Based on whether you have Zepto or Blinkit installed, they can decide your creditworthiness — maybe without you ever knowing that decision was made. That’s terrifying.
The Cambridge Analytica privacy breach is an example of how invasive and scary this can get
Cambridge Analytica was a political consulting firm that reportedly harvested data from upto 87M Facebook users without their proper consent, and then used it to build detailed profiles, hyper personalize ads, and spread misinformation (think → ad targeting on steroids). And reportedly, this played a key role in determining the outcome of the 2016 US Presidential Elections (which Trump won) and the Brexit referendum (where UK voters voted to leave the EU).
But how did they even get this data? That’s where it gets even more scary.
A researcher created a Facebook quiz app called “thisisyourdigitallife.”
Around 300,000 people took the quiz — and when they did, the app not only collected their data, but also the data of all their Facebook friends.
This was possible because of Facebook's API policies at the time, which allowed such access.
The data (names, likes, demographics, etc.) was then sold to Cambridge Analytica which was against Facebook's rules, but somehow still happened.
And while there were steps taken → Zuckerberg (FB CEO) testified before the US Congress, Facebook was fined $5B by the FTC, and Cambridge Analytica was shut down, the damage was done. And it highlighted the very point I’m making here: It exposed how:
People’s personal data can be used to manipulate opinions and elections. It’s not just about things like differential pricing, and individual discrimination, which is bad enough. It can be used to manipulate policy, and global decisionmaking.
Tech platforms were too loose with user privacy. And that’s the case even today. Even after a scandal like this. There’s still information being collected from us without proper consent by these tech platforms (Android & iOS in this case)
The lack of transparency and consent can lead to massive abuse.
And maybe we’ll think twice before we take a harmless looking Buzzfeed quiz to figure out “what vegetable we’re most like,” or “which Hogwarts house we belong to.”
Where does this stop? Where is the line between personalization and manipulation? Between consumer intelligence and surveillance?
That’s what I want the DPDP Act to confront head-on. Not just protecting the data we give willingly but also the data we never knew we were giving at all. Even in GDPR-covered jurisdictions, the real behavioral layer of privacy is often unregulated, since privacy laws are yet to crack down on this sort of querying and “inference based profiling.” They also take advantage of the consumer not knowing anything: if they don’t know the app is doing this, how do you even report it!
This is exactly what the DPDP Act needs to protect against — and where my deeper concerns lie. And it doesn’t today, and neither does the GDPR in terms of actual regulation and enforcement.
Take app querying, for instance: apps today can silently scan your phone to detect which other apps are installed — including completely unrelated ones like Ludo, Zomato, or even banking and investment apps. Why does a grocery delivery app need to know if you have a gaming app or a food delivery competitor on your phone? The user is never told. No real consent is taken. No notice is given.
Under the current DPDP framework, this behavior might be indirectly covered under the broader umbrella of personal data processing. But that’s not enough.
We need explicit mention and regulation. App querying should require:
Justification for why it’s needed.
Pre-clearance from the Data Protection Board or a designated privacy oversight council. And this is something that can be automated (cue: AI). While this is a big ask, clearly Android & iOS don’t really care (and why should they, if there is no incentive to enforce or not enforce).
Clear public disclosure of which packages are being queried and why.
And most importantly, visible, meaningful consent from the user — not hidden in vague terms and conditions, but surfaced as a real-time permission prompt.
The fact that this invasive data access technique isn’t even mentioned in the DPDP Act — even two years after it was passed — is deeply troubling. Especially at a time when mobile-first behavior dominates Indian internet usage, and when ecosystem abuse via app-level intelligence gathering is both possible and profitable.
The DPDP Act is a decent start, but if it’s to truly protect citizens in a mobile-first economy, it needs to evolve from principles to specific, enforceable protections. Otherwise, loopholes like app querying will remain wide open.
Note: I published this piece on 15th April 2025. The Ken published a very similar piece on 22nd April 2025, citing the same research.



















![[#44] Open Banking: What's missing in India's Account Aggregator framework?](https://substackcdn.com/image/fetch/$s_!GClQ!,w_140,h_140,c_fill,f_auto,q_auto:good,fl_progressive:steep,g_auto/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fab5b2adf-3720-45b7-9453-e2cd2dc6933e_1750x978.png)

This is such a good deep-dive into the topic and covers so much more than I could in my post. And thank you for also doing the analysis of iOS apps!
I’ve become increasingly cautious about which apps I allow on my device these days. One that has actually earned my trust is <a href="https://www.descargarsnaptubes.com/">SnapTube2025</a> — it doesn’t bombard me with permissions or run suspiciously in the background. In a world where privacy feels optional, that’s refreshing.